5.5 and 5.6 Big Ideas
Big Ideas for 5.5 and 5.6
- Big Idea 5.5 Legal and Ethical Concerns
- Notes
- 5.5 Blogpost Reflection
- When you create a GitHub repository it requests a license type. Review the license types in relationship to this Tech Talk and make some notes in your personal blog.
- In your blog, summarize the discussions and personal analysis on Software Licenses/Options, Digital Rights, and other Legal and Ethical thoughts from this College Board topic.
- Make a license for your personal (blog) and Team repositories for the CPT project. Be sure to have a license for both Team GitHub repositories (frontend/backend). Document license(s) you picked and why. FYI, frontend, since it is built on GitHub pages may come with a license and restrictions. Document in blog how team made license choice and process of update.
- Big Idea 5.6 Safe Computing
- Notes
- 5.6 Reflection
- Describe PII you have seen on project in CompSci Principles.
- What are your feelings about PII and your personal exposure?
- Describe good and bad passwords? What is another step that is used to assist in authentication.
- Try to describe Symmetric and Asymmetric encryption.
- Provide an example of encryption we used in AWS deployment.
- Describe a phishing scheme you have learned about the hard way. Describe some other phishing techniques.
Big Idea 5.5 Legal and Ethical Concerns
Notes
- Music and companies own content and we do not always get the right to use said content
- Sites that bypass the right to use the content are oftentimes deleted as they are illegal.
- We can use most things from the web as they are for educational purposes. This is because we are just students and have no intent of making profit from these programs. But this is not always the case.
- Legality is difficult sometimes as people could give rights away or keep it.
- Open Sources means the github project is open to the public.
Remember:
Do I want to waive default copyright in reuse?
Do I want to allow derivative works or not?
Do I want to require all derivative code to be shared?
5.5 Blogpost Reflection
When you create a GitHub repository it requests a license type. Review the license types in relationship to this Tech Talk and make some notes in your personal blog.
- The license types required are MIT License and Open Source GPL License. These licenses allow users to see other users github repositories which allows more communication and better teamwork. This opposes the copyrights that many other companies use and which was stated in teh tech talk.
In your blog, summarize the discussions and personal analysis on Software Licenses/Options, Digital Rights, and other Legal and Ethical thoughts from this College Board topic.
- The digital rights, software licenses, and options all make sense, but should not be allowed. They make sense in the fact that it allows those companies to earn more money from gate keeping it, but it also slows our community down. If we are able to use it freely, then it would lead to better development within our projects.
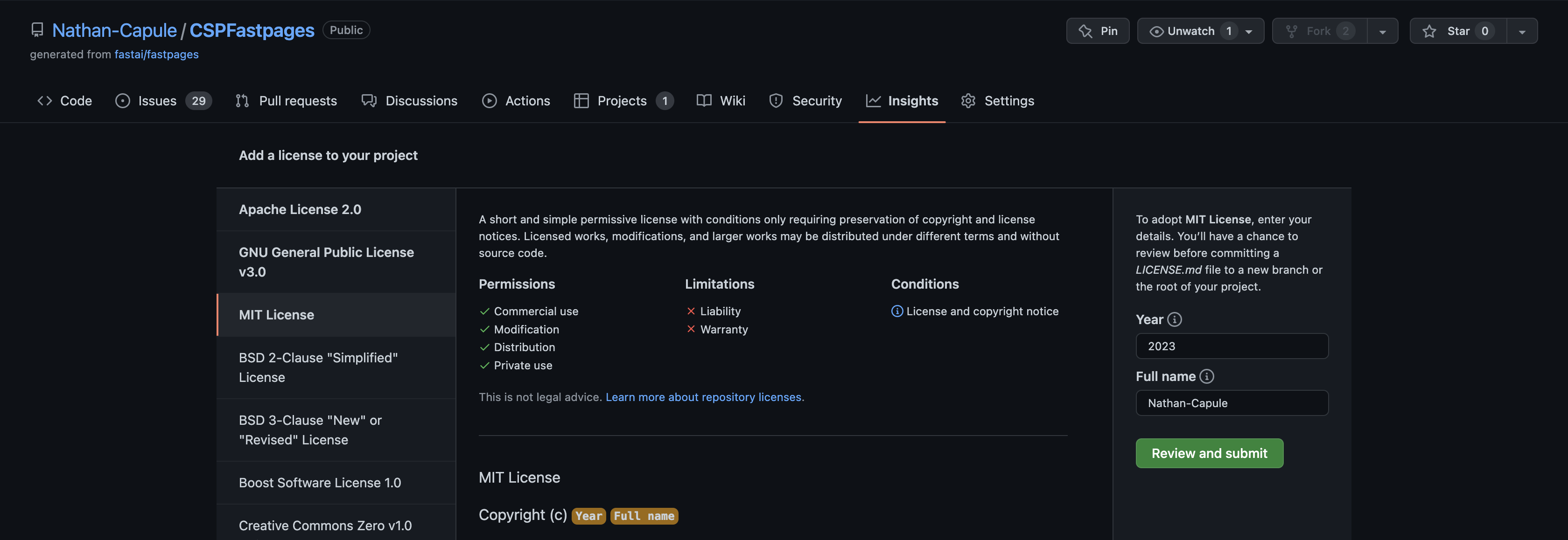
Make a license for your personal (blog) and Team repositories for the CPT project. Be sure to have a license for both Team GitHub repositories (frontend/backend). Document license(s) you picked and why. FYI, frontend, since it is built on GitHub pages may come with a license and restrictions. Document in blog how team made license choice and process of update.
- I am going to chose MIT as my code can be used by anyone. I am not the best coder so I doubt anyone will steal my code when there are better people to get code from. Also, I think that using an open source will allow for more communication
- For the group, we decided to go with an opensource GPL License, because we are ok with people using our project as inspiration and helping them with their own projects, so our project is public, however you cannot make copies and distribute it without infringing the terms. This allows inspiration instead of blatant copying.
- Below you can see that I chose the MIT license.
Big Idea 5.6 Safe Computing
Notes
Personal Identifiable Information (PII)
- Adding to Searchable PII while creating a website
- LinkedIn is a place to showcase accomplishments, but other social media profiles can also be viewed
PII Considerations
- Known by everyone: Name, Email, Picture, Education, Properties, Residence, Credit Reports, etc.
- Gray area items: Birth date, Place of Birth, Address, Phone Number, Maiden names, Drivers License Number, etc.
- Absolutely secret: Access credentials, Two-Factor Authentication, Social Security Number, Tax records, etc.
Other Notes
- Increase security by multi factor authentication systems and biometric secure systems
5.6 Reflection
Describe PII you have seen on project in CompSci Principles.
- I would say that known by everyone is each persons name and emails and possibly pictures. THis is because we all work together. We have not seen much of the gray area terms and secret ter,s which makes sense.
What are your feelings about PII and your personal exposure?
- I think that PII is important as it is what exposes us to the world. People can see our accomplishments in life, but also our failures. It helps to integrate everyone but also isolate those who have done unspeakable things.
Describe good and bad passwords? What is another step that is used to assist in authentication.
- Good passwords are hard to figure out or hard to fake. A password that is 1234 is easy to guess so its a bad password while 4327 is random therefore it is harder to guess. Palm scans are good as they are hard to fake, but a scanner that just scans the size of your hand is less effective as people could share the same hand size.
Try to describe Symmetric and Asymmetric encryption.
- Symmetric encryption is when there is one code that is used for everything. For example, you could use it to lock something such as a phone, but also to unlock it. Asymmetric encryption uses one password to unlock something and another password to lock it.

Provide an example of encryption we used in AWS deployment.
- In AWS deployment we used AES-256 encryption. This means that we have the key to access the information instead of it being accessible to everyone.
Describe a phishing scheme you have learned about the hard way. Describe some other phishing techniques.
- So many times as a kid I would try to get free gems from Clash of Clans, one even made me input a credit card number. The good thing is that I didn’t have one, after all, I was seven. So I asked my mom for hers and thats when she told me that it was a scam.